Install Gvlk Key Kmspico Portable
Is there some way to 'validate' software like KMSPico? I assume malware scanners are useless due to false positives deriving from calls to various hooks that seem 'suspicious'. I have a vague understanding of what KMS activators do, but is there a way to monitor the installation to make sure they aren't accessing random files on my hard drive or calling home to some place in Nigeria or Russia? In theory, software like this should be accessing very specific files and registry keys.
Is there a way to ensure nothing outside the scope of activation is being accessed? I've used the mini-KMS activator for years now, and haven't noticed any funny business.

But the truth is, if done correctly, I wouldn't really know anyway. How do people feel about software like this? Just to be sure, what's the canonical website for KMSPico • • • • •.
2nd Edition Introduction Reasoning And Writing. Jan 14, 2016 - 3 min - Uploaded by jon softI downloaded the KM Spico file off the website, I have Windows 10 on my tablet PC..
(Key Management Service) and (Multiple Activation Keys) are technologies Microsoft uses to activate devices deployed in bulk (e.g., in a corporate environment). The software running on these devices are in the volume license channel (what you buy off shelves are from the retail channel). MAK keys have a fixed number of activations associated with it and is used to activate a fixed number of devices by phoning back to Microsoft's servers.
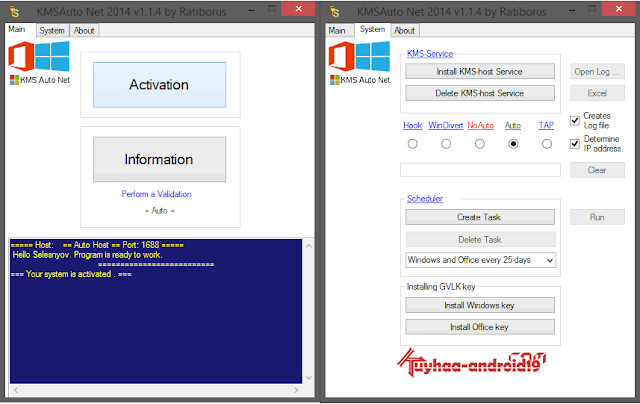
On the other hand, KMS is where a KMS client (device) activates by phoning to a KMS server on the local network rather than Microsoft's for various reasons (privacy, avoiding bombardment of Microsoft's servers, etcetera). What KMSpico does is to replace the installed key with a volume license key, create an emulated instance of a KMS server on your machine (or in previous iterations of the software, search for KMS servers online) and force the products to activate against this KMS server. On Windows 8, this works as intended and activation is straightforward. But Windows 8.1 changed things by not allowing localhost activation (or KMS requests to 127.0.0.1). To circumvent this, the three methods listed below in order of decreasing preference, are being currently employed.
• The first, and currently the best, is to inject a DLL to the activation process and patching it temporarily in-place to divert the activation request, bypassing the localhost check. This is fast and no permanent changes are written to the system. • The second method (and second best) is by using a service called WinDivert which is a packet redirector.
What is does is capture packets and seem like it came from a different IP, circumventing the localhost check. Since this installs a service and uses that for activation, it is slower than the first. • If none of the above works, the least recommended third method is used which is installing a TAP driver which creates a virtual network adapter and seem like the activation server comes from a different IP. This is a cumbersome and a clunky method. Since KMSpico (here's the, by the way), activates by passing off the localhost as a different IP, you might see some strange entries in your firewall's log.
This is safe and is normal. Furthermore, KMS activation only lasts for 180 days after which, it must be activated again. So if you install KMSpico, it creates an activation service that runs KMSpico twice a day to reset this counter. If you do not like this behaviour, KMSpico also comes in a portable flavour (which does not run in the background) where you have to manually run KMSpico once every 180 days. And if this doesn't instil confidence in KMSpico, you could always run it through to see what is being accessed and/or modified. Edit: Thank you very much, kind person, for the gold!
A wonderful surprise, indeed! FWIW, I did the same thing, so don't feel bad. Basically, I Googled, chose the first result (which had a domain name that sounded KMSPico official) and mindlessly installed the exe.
When the website started polling me about how many hours I spend on the internet, I started to suspect I probably did a really stupid thing. Lo and behold, it installed crapware on my computer.
It wasn't outwardly malign -- a search bar, some kind of ad targeting thing. It was actually pretty easy to get rid of, but who knows what else was done behind the scenes. Reformatted my drive and did it the right way the second time. Depending on the kind of software you want to 'unlock', kmspico should be the last resort. For Office 2013 and Win8, there are no better ways to activate them, but for Win7 there is Daz's Loader and for Office 2010 there is a specific site which posts new MSDNAA keys every few days, which can be activated over the phone most of the time. I generally prefer activation methods, that don't require software to be running constantly in the background.
Luckily I have a Dreamspark account, so I don't need anything for my Win8 Install. There are people selling keys on the cheap for Win8 and Office 2013 that they got from a MSDN account. These will activate the software the 'official way', but are still no legitimate licenses.
If you don't care about legitimacy (like me), you could buy one of those keys. The Regulation Of International Trade 4th Edition here. Hey there -- thanks for answering. I guess my question wasn't popular. The private trackers I use are bitme, demonoid, tvtorrents, what.cd, and waffles. I suppose demonoid isn't really private per se, though since their torrents are de facto public.
I guess I'm coming at it from a bigger POV. I've read a lot of comments about people experiencing bad stuff from mini-KMS and KMSpico which sound like viral infections, or at least, it has unintended consequences.
From a technical standpoint, I understand what KMS activators do, more or less. I was wondering if there's a way to catch any unintended consequences. Since I now have a job, I no longer have the time to investigate things like searching for strings in binaries, using Zone Alarm to catch calling home, looking at system calls which may be out of scope of the intended purpose, etc. Is there a private tracker with a sophisticated user base in particular that you'd recommend for applications?
We had a KMS host working wonderfully on a VM. I then converted that VM to make the disks thin. Then the host stopped accepting activations. I have uninstalled the KMS key and setup KMS host again on the same machine with no luck. The DNS entry shows up in DNS correctly. The Windows firewall is not on on any machine in our domain and there is no other firewall between the KMS host and the clients.
The only change, other than some updates was the conversion to thin disks. Has anyone come across this issue? Here is the results of the slmgr.vbs /dlv: C: Windows System32>cscript slmgr.vbs /dlv Microsoft (R) Windows Script Host Version 5.8 Copyright (C) Microsoft Corporation. All rights reserved.